22+ Computer Networks And Cybersecurity Pdf
Military news updates including military gear and equipment breaking news international news and more. A Guide to IEEE 80211i.

Cyber Security Body Of Knowledge And Curricula Development Intechopen
AMC Networks Restructuring To Result in 350-475 Million Charge.

. Web The Stop Online Piracy Act SOPA was a controversial proposed United States congressional bill to expand the ability of US. May 24 2022 Our panel of authors and CISOs discuss the 2022 Data Breach Investigations Report and how the changing cyber threat landscape requires organizations to react quickly. By Jon Lafayette published 1 December 22.
Law enforcement to combat online copyright infringement and online trafficking in counterfeit goodsIntroduced on October 26 2011 by Representative Lamar Smith R-TX provisions included the requesting of court orders to. California voters have now received their mail ballots and the November 8 general election has entered its final stage. Establishing Wireless Robust Security Networks.
Web Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. Web Key Findings. The expression dates back from the first decade of the diffusion of the internet.
Web Category 3 Networks that utilized affected versions of SolarWinds Orion and have evidence of follow-on threat actor activity. At a minimum grayware behaves in an annoying or undesirable manner and at worst monitors the system and phones home with information. Web Cyberspace is a concept describing a widespread interconnected digital technology.
This marks a milestone in delivering new value for Office 365 subscribers with a focus on collaboration apps that work for you a perfect pairing with Windows 10 and security features businesses will love. For the purposes of ED 21-01 and associated supplemental guidance a network is defined as any computer network with hosts that share either a logical trust or any account credentials with SolarWinds Orion. Web Computer security cybersecurity cyber security or information technology security IT security is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure theft of or damage to hardware software or data as well as from the disruption or misdirection of the services.
State Local Tribal and Territorial SLTT government organizations we cultivate a collaborative environment for information sharing in support of our missionWe offer members incident response and remediation support through our team of security experts and develop. Web The CERT Division is a leader in cybersecurity. It also covers sensors and other devices such as programmable logic controllers which interface with process plant or machinery.
Web Cybersecurity Cyber_Security 1 protects computers servers and networks from intrusion theft and other forms of harm to their data hardware and software as well as from interruptions in. Web Further the UN R155 Cybersecurity Regulation 1 and the ISOSAE 21434 2 are analyzed to provide the state of the art about ongoing cybersecurity standardization and regulation efforts in the. Web The sections below offer an overview of our findings in order to aid targeted entities in Ukraine as well as cybersecurity organizations in defending against this threat group.
Web The Business Journals features local business news from 40-plus cities across the nation. Web Since at least March 2016 Russian government cyber actorshereafter referred to as threat actorstargeted government entities and multiple US. Web Wireshark is the worlds foremost and widely-used network protocol analyzer.
Web The new Office is here Today is the worldwide release of Office 2016 for Windows. SP 800-97 Establishing Wireless Robust Security Networks. Web The term grayware was coined in September 2004 and describes unwanted applications or files that arent malware but worsen the performance of the computer and can cause cybersecurity risk.
In cyberspace people can hide behind fake identities as in the famous The New Yorker cartoon. Amid rising prices and economic uncertaintyas well as deep partisan divisions over social and political issuesCalifornians are processing a great deal of information to help them choose state constitutional. Web MS-ISAC at a glance.
Our services are intended for corporate subscribers and you warrant. Web Symantec security research centers around the world provide unparalleled analysis of and protection from IT security threats that include malware security risks vulnerabilities and spam. When we originally published this report we noted While we have mapped out three large clusters of currently active Gamaredon infrastructure we.
It lets you see whats happening on your network at a microscopic level and is the de facto and often de jure standard across many commercial and non-profit enterprises government agencies and educational institutions. Web According to the BLS Job Outlook employment for computer hardware engineers the expected ten-year growth from 2019 to 2029 for computer hardware engineering was an estimated 2 and a total of 71100 jobsSlower than average in their own words when compared to other occupations. Thomas Umstead published 2 December 22.
2022 DBIR CISO Panel. We partner with government industry law enforcement and academia to improve the security and resilience of computer systems and networks. Web Supervisory control and data acquisition SCADA is a control system architecture comprising computers networked data communications and graphical user interfaces for high-level supervision of machines and processes.
We also provide tools to help businesses grow network and hire. We study problems that have widespread cybersecurity implications and develop advanced methods and tools to counter large-scale sophisticated cyber threats. It refers to the online world as a world apart as distinct from everyday reality.
Web In the current age of the Fourth Industrial Revolution 4IR or Industry 40 the digital world has a wealth of data such as Internet of Things IoT data cybersecurity data mobile data business data social media data health data etc. To intelligently analyze these data and develop the corresponding smart and automated applications the. Web Visit our privacy policy for more information about our services how New Statesman Media Group may use process and share your personal data including information on your rights in respect of your personal data and how you can unsubscribe from future marketing communications.
As a trusted cybersecurity partner for 13000 US. A Guide to IEEE 80211i. A look at the weekends top TV sports events on broadcast cable and streaming services Surface Gets Second Season on Apple TV Plus.
Critical infrastructure sectors including the energy nuclear commercial facilities water aviation and critical manufacturing sectors. Web Join our panel of cybersecurity experts as they discuss key findingsand what they mean for the cybersecurity industry. This is a decrease from the 2014 to 2024 BLS.
Web Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations.

Free 17 Sample Security Reports In Ms Word Pages Google Docs Pdf

Hacking And Defending Apis Red And Blue Make Purple Pdf
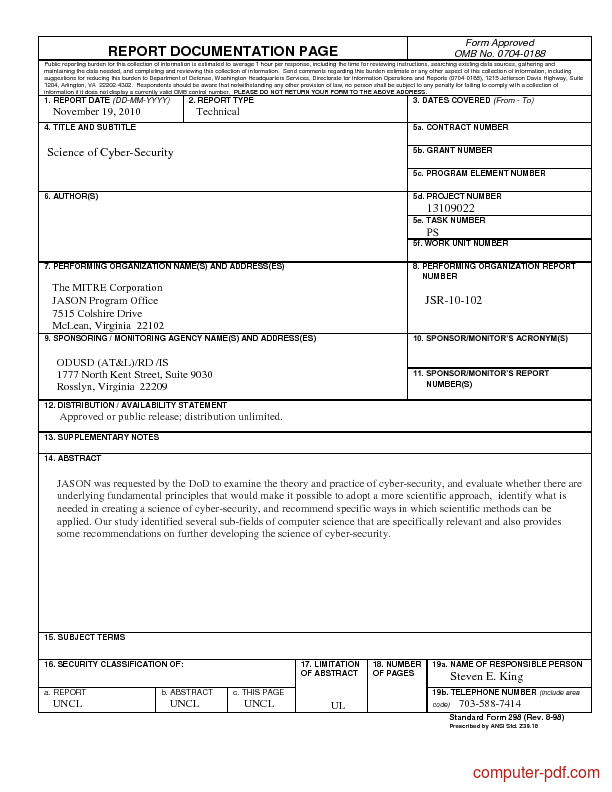
Pdf Science Of Cybersecurity Free Tutorial For Beginners

Pdf Revisiting Cyber Definition
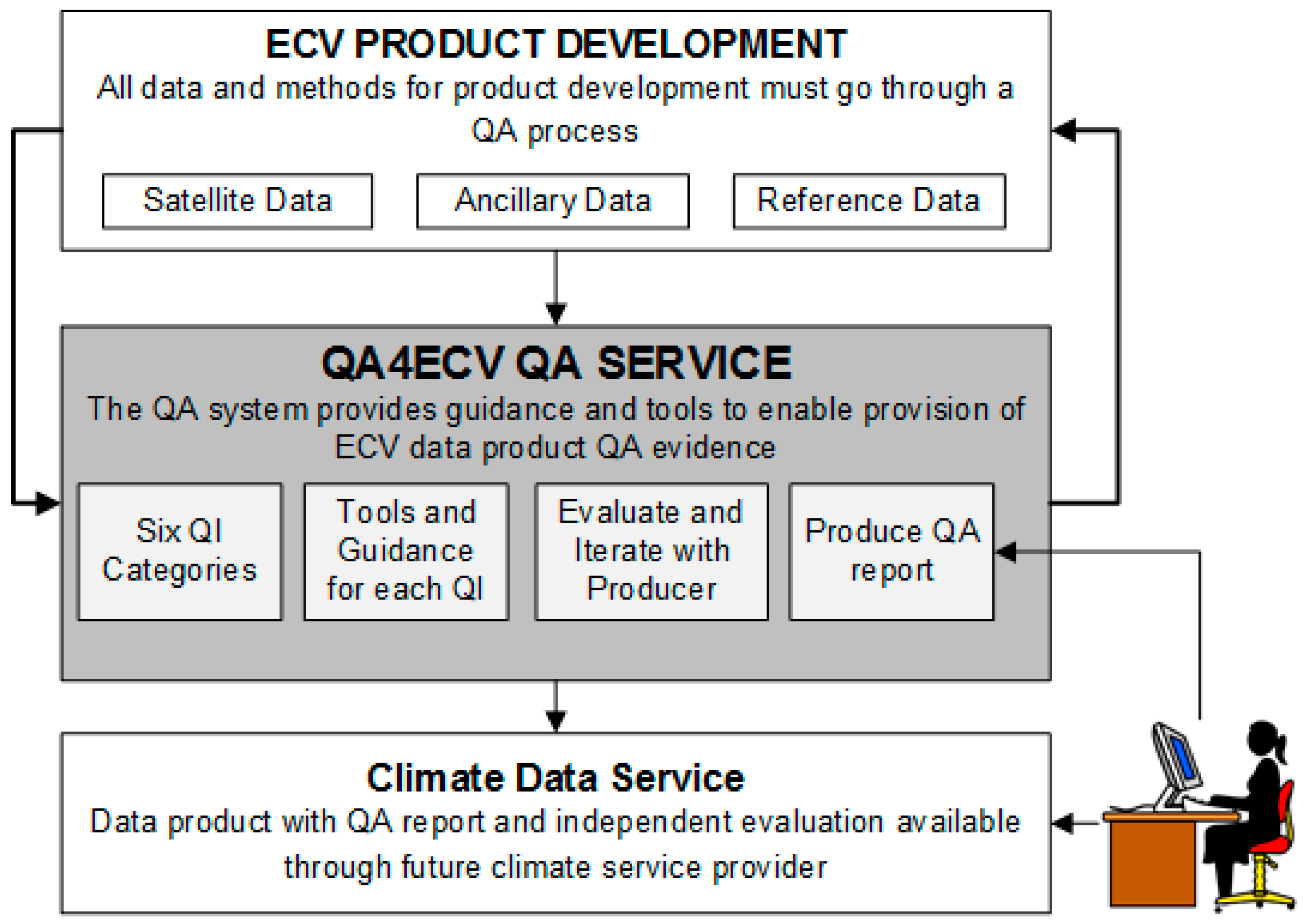
Remote Sensing Free Full Text Quality Assurance Framework Development Based On Six New Ecv Data Products To Enhance User Confidence For Climate Applications

Cyber Security University Of London

Pdf Computer Networks Information Security

Columbus State Community College

Free Cyber Security Books Pdf Free Download 7 Cyber Security Pdf Free Pdf Books

Download Computer Network Security Pdf Snabay Networking

Globexdatacompanyinfoen 231219 Pdf Encryption Computer Security
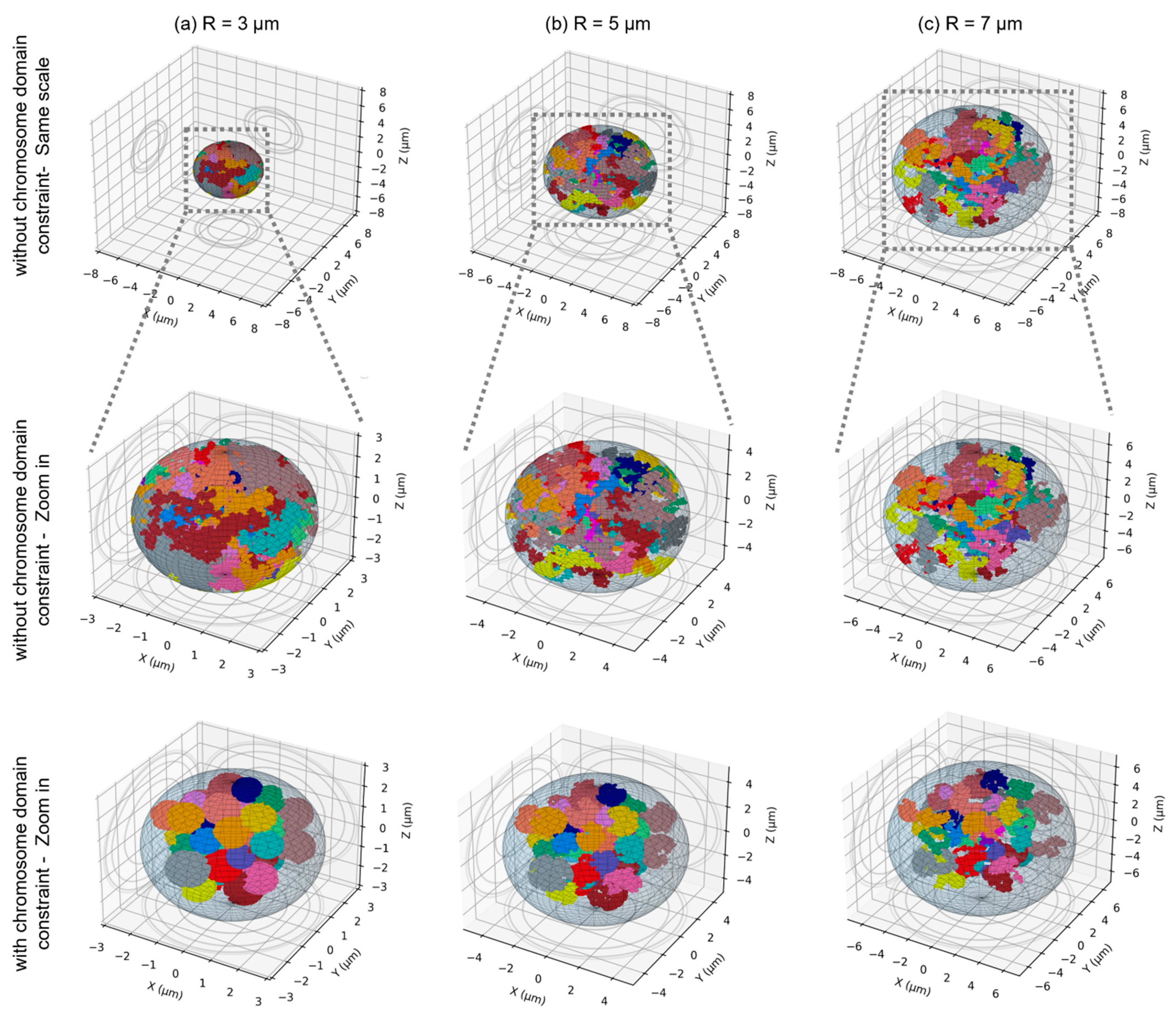
Ijms Free Full Text Geometrical Properties Of The Nucleus And Chromosome Intermingling Are Possible Major Parameters Of Chromosome Aberration Formation

What Is Protective Security Ps Springerlink

Free 13 Security Incident Response Plan Samples In Ms Word Pdf
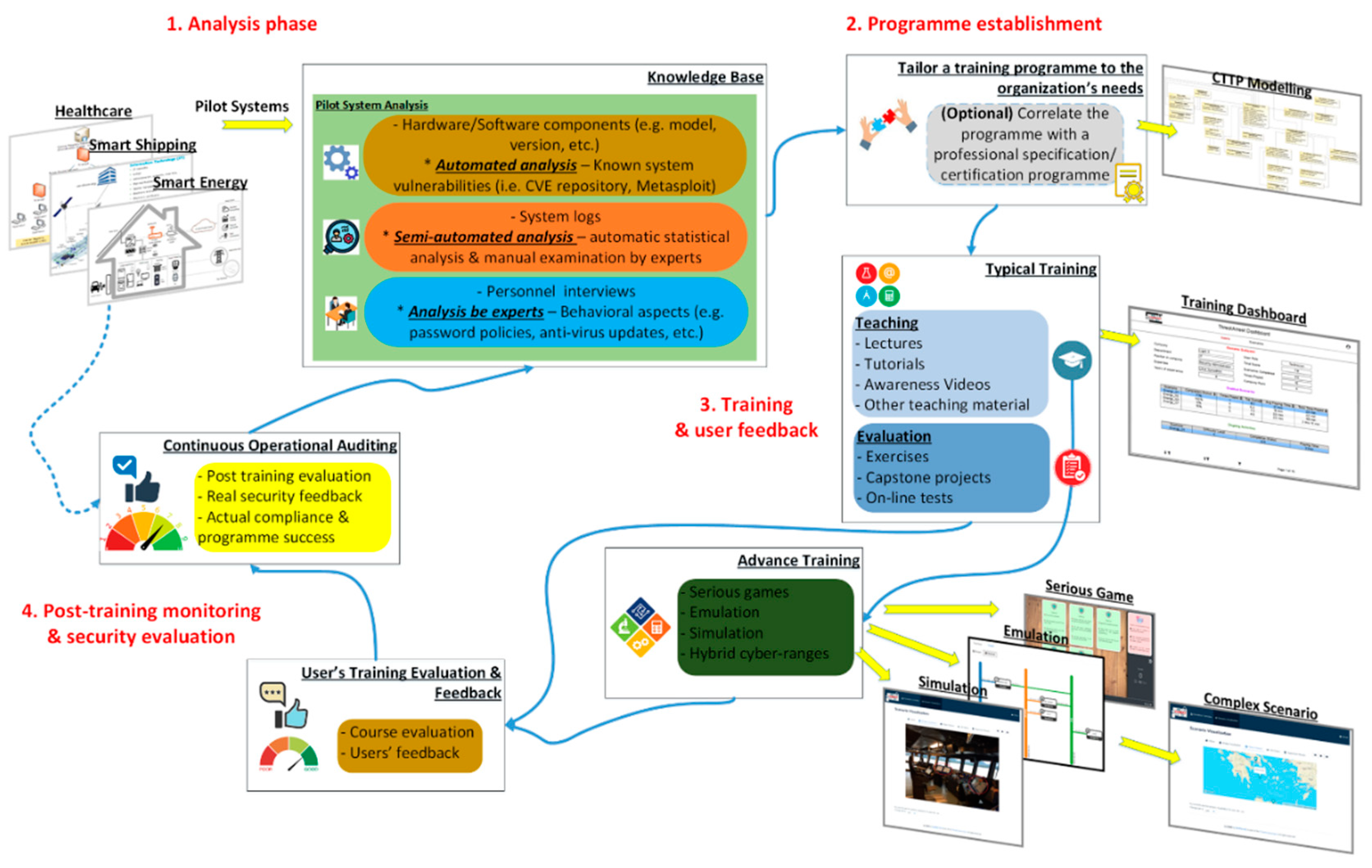
Applied Sciences Free Full Text Modern Aspects Of Cyber Security Training And Continuous Adaptation Of Programmes To Trainees
Cyber Security Practitioner S Guide

Module 2 Computer Networks And Security Pdf Data Transmission Modulation